Webserver installieren:
apt-get update
apt-get install apache2 apache2-utils apache2.2-bin apache2.2-common libapache2-mod-php5
MySQL Datenbankserver installieren:
apt-get install mysql-client mysql-common mysql-server libmysqlclient-dev
während der Installation müssen Sie ein Passwort für den User 'root' vergeben.
Dieses Kennwort wird uns noch lange begleiten...
Installation von Abhängigkeiten:
apt-get install g++ make autoconf automake libtool flex bison gcc libnet1 libnet1-dev libcrypt-ssleay-perl libpcre3 libpcre3-dev libphp-adodb libssl-dev libtool libwww-perl ntp php5-cli php5-gd php5-mysql php-pear
Installation von Abhängigkeiten für SNORT:
cd /usr/src
wget http://www.tcpdump.org/release/libpcap-1.3.0.tar.gz
wget http://libdnet.googlecode.com/files/libdnet-1.12.tgz
wget http://www.snort.org/dl/snort-current/daq-1.1.1.tar.gz
tar -zxf libpcap-1.3.0.tar.gz
tar -zxf libdnet-1.12.tgz
tar -zxf daq-1.1.1.tar.gz
rm *.tgz && rm *.tar.gz
cd libpcap-1.3.0 &&./configure --prefix=/usr --enable-shared && make && make install
cd ../libdnet-1.12 && ./configure --prefix=/usr --enable-shared && make && make install
cd ../daq-1.1.1 && ./configure && make && make install
Library-Pfad aktualisieren:
echo >> /etc/ld.so.conf /usr/lib
echo >> /etc/ld.so.conf /usr/local/lib && ldconfig
Snort installieren und einrichten:
cd /usr/src
wget http://nbhcrew.de/zmod/downloads/Configs/snort.conf
wget http://nbhcrew.de/zmod/downloads/Configs/local.rules
wget http://nbhcrew.de/zmod/downloads/Configs/barnyard2.conf
wget http://www.snort.org/dl/snort-current/snort-2.9.3.1.tar.gz -O snort-2.9.3.1.tar.gz
tar -zxf snort-2.9.3.1.tar.gz && cd snort-2.9.3.1 && rm ../*.tar.gz
./configure --enable-sourcefire && make && make install
mkdir /etc/snort /etc/snort/rules /var/log/snort /var/log/barnyard2 /usr/local/lib/snort_dynamicrules
touch /etc/snort/rules/white_list.rules /etc/snort/rules/black_list.rules /etc/snort/rules/local.rules
groupadd snort && useradd -g snort snort
chown snort:snort /var/log/snort /var/log/barnyard2
cp /usr/src/snort-2.9.3.1/etc/*.conf* /etc/snort
cp /usr/src/snort-2.9.3.1/etc/*.map /etc/snort
cp /usr/src/snort.conf /etc/snort
cp /usr/src/local.rules /etc/snort/rules
Snort starten und einen ersten Ping-Test ausführen:
/usr/local/bin/snort -A console -q -u snort -g snort -c /etc/snort/snort.conf -i eth0
Barnyard2 installieren (Schnittstelle für Snort)
cd /usr/src && wget https://github.com/firnsy/barnyard2/tarball/master
tar -zxf master && cd firnsy-barnyard2-*
autoreconf -fvi -I ./m4
./configure --with-mysql && make && make install
cp /usr/src/barnyard2.conf /etc/snort
cp schemas/create_mysql /usr/src
MYSQL konfigurieren:
mysql -uroot -pPASS
create database snort;
create database archive;
grant usage on snort.* to snort@localhost; grant usage on snort.* to snort@127.0.0.1;
grant usage on archive.* to snort@localhost; grant usage on archive.* to snort@127.0.0.1;
set password for snort@localhost=PASSWORD('PASS');
grant all privileges on snort.* to snort@localhost;
grant all privileges on snort.* to snort@127.0.0.1;
grant all privileges on archive.* to snort@localhost;
flush privileges;
use snort;
source /usr/src/create_mysql
exit
Testen von Snort mit Barnyard2:
/usr/local/bin/barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /etc/snort/bylog.waldo -G /etc/snort/gen-msg.map -S /etc/snort/sid-msg.map -C /etc/snort/classification.config &
Services installieren:
touch /etc/init.d/snortbarn
nano /etc/init.d/snortbarn
#! /bin/sh
#set -x
#
### BEGIN INIT INFO
# Provides: snortbarn
# Required-Start: $remote_fs $syslog mysql
# Required-Stop: $remote_fs $syslog
# Default-Start: 2 3 4 5
# Default-Stop: 0 1 6
# X-Interactive: true
# Short-Description: Start Snort and Barnyard
### END INIT INFO
. /lib/init/vars.sh
. /lib/lsb/init-functions
do_start()
{
log_daemon_msg "Starting Snort and Barnyard" ""
/sbin/ifconfig eth0 up
/usr/local/bin/snort -q -u snort -g snort -c /etc/snort/snort.conf -i eth0 &
/usr/local/bin/barnyard2 -q -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /etc/snort/bylog.waldo -G /etc/snort/gen-msg.map –S /etc/snort/sid-msg.map -C /etc/snort/classification.config 2> /dev/null &
log_end_msg 0
return 0
}
do_stop()
{
log_daemon_msg "Stopping Snort and Barnyard" ""
kill $(pidof snort) 2> /dev/null
kill $(pidof barnyard2) 2> /dev/null
log_end_msg 0
return 0
}
case "$1" in
start)
do_start
;;
stop)
do_stop
;;
restart)
do_stop
do_start
;;
*)
echo "Usage: snort-barn {start|stop|restart}" >&2
exit 3
;;
esac
exit 0
chmod +x /etc/init.d/snortbarn
update-rc.d snortbarn defaults
CleanUp:
rm /var/www/index.html
pkill snort && pkill barnyard2
rm -rf /var/log/snort/* /var/log/barnyard2/*
sudo service snortbarn start
Nano /etc/snort/snort.conf
Zeile 553: include $RULE_PATH/snort.rules
sudo service snortbarn start
Regeln aktualisieren:
Bei www.snort.org registrieren und einen Oinkcode beschaffen .
cd /usr/src && wget http://pulledpork.googlecode.com/files/pulledpork-0.6.1.tar.gz
tar -zxf pulledpork-0.6.1.tar.gz && cd pulledpork-0.6.1
cp pulledpork.pl /usr/local/bin && cp etc/*.conf /etc/snort
Edit "/etc/snort/pulledpork.conf":
Comment out lines 22 & 26
Line 20: enter your “oinkcode” where appropriate or comment out the line if you didn’t get one above
Line 23: leave alone (uncommented) to use the Emerging Threats rule set
Line 71: change to: rule_path=/etc/snort/rules/snort.rules
Line 86: change to: local_rules =/etc/snort/rules/local.rules
Line 89: change to: sid_msg=/etc/snort/sid-msg.map
Line 112: change to: config_path=/etc/snort/snort.conf
Line 124: change to: distro=Debian-Lenny
Line 171: Uncomment and change to: enablesid=/etc/snort/enablesid.conf
Line 173: Uncomment and change to: disablesid=/etc/snort/disablesid.conf
Line 174: Uncomment and change to: modifysid=/etc/snort/modifysid.conf
/usr/local/bin/pulledpork.pl -c /etc/snort/pulledpork.conf -T -l
apt-get install Nikto
perl nikto.pl -h HOST -p PORT
Installation von SNORBY:
(geht jetzt endlich!)
echo "gem: --no-rdoc --no-ri" >> ~/.gemrc
curl -L https://get.rvm.io | bash -s stable --ruby --rails
source /usr/local/rvm/scripts/rvm
rvm autolibs enable
rvm pkg install openssl
rvm install 1.9.2 --with-openssl-dir=$HOME/.rvm/usr
aptitude install -y imagemagick wkhtmltopdf openjdk-6-jdk
aptitude install -y make unzip git libxml2-dev libxslt1-dev libmysqlclient-dev g++ libmagickcore-dev libmagickwand-dev libcurl4-openssl-dev libssl-dev apache2-prefork-dev libapr1-dev libaprutil1-dev build-essential openssl libreadline6 libreadline6-dev curl git-core zlib1g zlib1g-dev libssl-dev libyaml-dev libsqlite3-0 libsqlite3-dev sqlite3 libxml2-dev libxslt-dev autoconf libc6-dev ncurses-dev automake libtool bison subversion libiconv libiconv-dev
gem install rails
gem install pdfkit
gem install rake
cd /var/www
git clone http://github.com/Snorby/snorby.git
cd config
bundle install
cp database.yml.example database.yml
cp snorby_config.yml.example snorby_config.yml
database.yml konfigurieren
sed -i "s|username:.*|username: root|g" database.yml
sed -i "s|password:.*|password: Password|g" database.yml
sed -i "s|host:.*|host: localhost|g" database.yml
sed -i "s|database:.*|database: snorby|g" database.yml
config.yml konfigurieren
sed -i "s|domain:.*|domain: localhost:3000|g" snorby_config.yml
rake snorby:setup
cd/var/www/snorby/
bundle exec rails server -e production
Dann zu der Seite:
http://IP-DES-RASPBERRY:3000 gehen
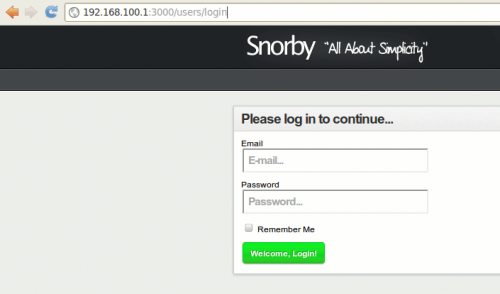
und einloggen mit
- Benutzername: snorby@snorby.org
- Passwort: snorby
Links:
howto-guide-to-snort-ids-in-debian
Snorby
https://snorby.org/